- Power BI continues to invest in empowering every individual, team, and organization to drive a data culture. Creation experience is improved by aligning our experiences with Office and enabling datasets authoring on the web.
- By bringing power query diagram view into Power BI Desktop, creators can use a no code experience to perform extract transform load (ETL) on their data.
- For teams, there are enhancements to metrics focused on enterprise needs and integration with Microsoft Viva Goals.
- The big data experience is increased through:
- automatic aggregations,
- query scale out,
- data protection capabilities via data loss prevention (DLP),
- improved visibility into activity to admins.
- Power Apps will expand governance capabilities to allow organizations to enable, manage, and support citizen development across the entire organization.
- Makers and developers of all skill levels will be more productive over Dataverse in a unified studio, with modern experiences to build and manage data and logic.
- Infused intelligence will: support development, enrich data, and optimize end-user experiences.
- In addition to ensuring trust and the ability to leverage rich data experiences, both makers and end-users will benefit from out-of-the-box collaboration capabilities to enable users to be more productive when working together.
- Power Pages brings more out-of-the-box capabilities to support both low-code/no-code development as well professional developers.
- In this release makers have additional capabilities to work with forms and lists and to use the design studio to get started quickly with additional solution templates.
- There are enhancements for professional developers to do more with the sites and to use both the Microsoft Power Platform command line interface (CLI) tool and visual studio (VS) Code
- Administrators can also use those tools to better administer and govern their Power Pages sites.
- Power Automate is more accessible with new experiences to help users of every skill level to build out their cloud and desktop flows.
- Organizations can automate their deployments of Power Automate, with additional enhancements for application lifecycle management (ALM).
- For increased usage of robotic process automation (RPA), new features will make it easier to manage machines in Azure and the credentials of your users and accounts.
- Power Virtual Agents bring improvements in:
- the authoring experience with commenting,
- Power Pages integration, data loss prevention options, proactive bot update messaging in Teams, and more.
- Creating a bot is typically a complex and time-intensive process, requiring long content update cycles and a team of experts.
- Power Virtual Agents gives anyone in your organization the ability to create powerful custom bots using an easy, code-free graphical interface, without the need for AI experts, data scientists, or teams of developers.
- A bot can interact with users, ask for clarifying information, and ultimately answer a user’s questions.
- AI Builder continues to enable citizen developers to use and customize AI capabilities to build more intelligent apps and workflows. Lifecycle and governance of AI Builder models will be improved with enhanced versioning, deployment, and monitoring capabilities.
- Makers will also benefit from new features for intelligent document and text processing like the ability to manage human in-the-loop validation, easier integration of large data sets for automated e-mail processing, and the ability to process contracts and multi-page tables in documents.
Power Apps Wave 2 2022 enhancements
July 13th, 2022 by Stephen Jones No comments »Dynamics 365 – Wave 2 highlights for 2022
July 13th, 2022 by Stephen Jones No comments »- Dynamics 365 Marketing brings real-time customer journey orchestration to enable business-to-business (B2B) brands to hyper-personalize experiences across the entire buying journey.
- Confidently grow your marketing and customer experience programs to target up to 100 million customers with up to 300 million messages and interactions per month.
- Intuitive lead capture forms, leads nurturing hands-off automation, and a new analytics dashboard enable alignment between sales and marketing teams like never before.
- Organizations can reach new levels of marketing maturity with AI-powered next best content selection and increased support for business units.
- Dynamics 365 Sales continues to optimize the seller experience using data and AI .
- Help sellers to prioritize their work, blending business with productivity tools to meet sellers where they are.
- Drive in-the-moment, collaboration experiences, so that every seller can engage with their colleagues and customers efficiently, reclaiming their time and being more productive.
- Dynamics 365 Customer Service is focused on delivering the capabilities that help run contact centers optimally.
- Enhancements in unified routing with features such as percentage-based routing, preferred agent routing, and longest idle routing are new features
- Customer support swarming in Microsoft Teams will help agents resolve complex cases through collaboration.
- Organizations can empower their customers with options to leave voicemail, callback, and dial agents directly in the voice channel.
- The agent experience is modernized with an enhanced conversation timeline, horizontal multisession navigation, and AI-powered conversation summary.
- Supervisors can view Microsoft Power Virtual Agents analytics within their omnichannel analytics dashboards.
- Dynamics 365 Field Service brings new capabilities that enable organizations to better orchestrate service operations for workers. Organizations can now:
- build and maintain location and assets for large facilities,
- keep their cost at bay by configuring “not to exceed” limits,
- and group similar incident types under “trade” for ease of management.
- Optimization improvements include booking lock constraints and i myriad of user experience improvements to the mobile app to further empower frontline workers.
- Dynamics 365 Finance launches the general availability of vendor invoice optical character recognition (OCR) which automates the reading and recognition of vendor invoices.
- There are additional capabilities for subscription billing use cases.
- The Tax calculation service will be integrated with Dynamics 365 Project Operations (preview)
- The electronic invoicing service will be extended to support new and upcoming e-invoice legislations for: France, Poland, and Saudi Arabia.
- Dynamics 365 Supply Chain Management continues to invest in capabilities that drive agility and resilience across the supply chain.
- New analytics and support for multiple vendors in planning optimization help organizations optimize their sourcing strategies.’
- Inventory visibility lets organizations track real-time consumption within allocated quantities in support of promotions, special events, and new product introductions.
- Guided warehouse implementation and configuration experiences enable rapid reconfiguration of supply chains .
- Manufacturers in the process industry can use Planning Optimization to shorten their planning cycles.
- Dynamics 365 Intelligent Order Management expands its ecosystem of providers and builds on the continued success of FedEx. There are now 14 providers that span the supply chain lifecycle from order ingestion to last-mile delivery.
- In the upcoming release, there is support for various order types—back orders, subscription orders, manual orders, and purchase orders.
- You can also simulate fulfillment to model and understand the impact of choosing various fulfillment strategies.
- Contextual collaboration features allow an order to be shared with multiple stakeholders using embedded Microsoft Teams.
- Dynamics 365 Project Operations Empower project managers and project teams in this release wave with project budgeting and time-phased forecasting, baselines and snapshots,
- The application experiences on the web and mobile form factors is modernised.
- For both project accountants and back-office personas, w advanced subcontracting and subscription billing capabilities are added.
- Across-the-board investments will ease the complexity of interaction patterns.
- Modern and fluent controls are also targeted for this release wave.
- Dynamics 365 Guides Improve collaboration experiences for authors and operators on Microsoft HoloLens 2.
- The application will also be updated to provide more advanced content authoring workflows versioning and publishing of guides in the coming wave.
- Dynamics 365 Human Resources We can now to tailor experiences and automatically complete processes where manual decisions and tasks are needed today.
- Improved efficiency is available to managers and employees by providing notifications outside of the application for benefits processes and tasks.
- Integrating employee skill and compensation, and leaving information to resource managers in Dynamics 365 Project Operations will also improve collaboration and efficiency.
- Dynamics 365 Commerce New and updated B2B experiences, include sales agreements across channels and customer-specific catalogs.
- Omnichannel media management features streamline workflows.
- Key point of sale investments includes a Store Commerce app availability for iOS and Android devices.
- Apple Pay and Google Pay digital wallet integration,
- New customer support options through virtual agent and live agent integration will be available for e-commerce.
- Dynamics 365 Fraud Protection will offer a new transaction acceptance booster (TAB) offering that allows merchants to increase their bank approval rates without having to rip and replace their incumbent fraud provider solution.
- To replace a merchant’s incumbent fraud solution is costly and timely, and this enables the merchant to benefit from Dynamics 365 Fraud Protection TAB capabilities with minimal disruption to their business.
- Dynamics 365 Business Central continues to improve the reporting capabilities for customers, including new report datasets for Excel and improvements to the Microsoft Power BI reports which now will support dimensions.
- The Microsoft Power Apps and Microsoft Power Automate integration offer new capabilities for low-code development.
- The application will get several improvements like: helping users do reverse entries in the payment reconciliation journal and several improvements to the supply chain functionality.
- There are steps to scale productivity via more efficient and performant tooling for development and administration.
- Dynamics 365 Customer Insights continues to invest in accelerating customer understanding by enhancing time to value with quicker out-of-the-box insights, predictions, segments, and measures with limitless extensibility across technology ecosystems.
- New features will power personalized experiences with real-time insights, analytics, and activations to deliver industry-leading personalization and moments-based marketing.
- New features also enable ubiquitous insights for an integrated data flow across Microsoft Dataverse, Dynamics 365, and Microsoft Power Platform for seamless workflows.
- Dynamics 365 Connected Spaces now supports alerts and notifications via Teams or Outlook when business AI-skills detect actionable patterns within a physical space.
- Customers can now use Dynamics 365 Connected Spaces in Germany (besides US and UK) and connect up to 10 cameras for each Azure Stack Edge device maximizing their existing investments in expanding Dynamics 365 Connected Spaces across their physical footprint.
- Customers can also leverage the Azure Stack Edge Pro 2 device for configuring Dynamics 365 Connected Spaces at the edge in addition to the existing Pro 1 devices.
Microsoft Purview – a family of data governance, risk, and compliance solutions
June 28th, 2022 by Stephen Jones No comments »The worldwide shift to a hybrid workplace has pushed us all to embrace ubiquitous connectivity. New connections help us to be more collaborative; and to routinely edit and share documents in real-time from wherever we work. Instant messaging a tool of convenience is now a cornerstone of communication. People in business, operations, and technical roles are adept at combining disparate solutions to meet changing needs. Multiple mobile and smart devices, go beyond secure corporate networks.
Constant connectivity brings evolving, inherent risks. Organizations have seen a massive increase in their digital footprint, often with data fragmentation and growth across a multitude of applications, devices, and locations. Dark data, which organizations pay to store, but goes underutilized in decision making, is growing at a rate of 62 percent per year. The virtual office and new collaboration mediums open doors to harassment, sensitive data leaks, and other workplace policy infractions. It’s a big digital world for any organization to manage.
Microsoft Purview is a family of data governance, risk, and compliance solutions that can help your organization to govern, to protect, and to manage your entire data estate. Microsoft Purview solutions provide integrated coverage and help address the recent increases in remote user connectivity, the fragmentation of data across organizations, and the blurring of traditional IT management roles.
Microsoft Purview combines the former Azure Purview and Microsoft 365 compliance solutions and services together into a single brand. Together, these solutions help your organization to:
- Gain visibility into data assets across your organization
- Enable access to your data, security, and risk solutions
- Safeguard and manage sensitive data across clouds, apps, and endpoints
- Manage end-to-end data risks and regulatory compliance
- Empower your organization to govern, protect, and manage data in new, comprehensive ways
Comodo Scores 100% in Endpoint and Internet Security Detection Tests – Ask Synergy Software Systems
June 25th, 2022 by Stephen Jones No comments »Comodo is the only Endpoint Protection company that is brave enough to publicly announce 100% protection against Ransomware and Malware for your endpoints.
Such a bold statement!!! We will be happy to demonstrate the unprecedented technology behind this statement (Valkyrie AI-based Auto Containment).
In March of 2022, AVLAB completed the 17th edition of its Advanced In The Wild Malware Test. Ten endpoint protection products were continuously evaluated, using thousands of unique malware samples to challenge the solutions against real-world threats. Products needed to demonstrate their capabilities using all components and protection layers.
Both Comodo’s Advanced Endpoint Security and Internet Security solutions received top honors with a recognition of ‘Excellent’. The products blocked all 2,050 possible threats and provided protection against all 0-day samples. Comodo’s Advanced Endpoint Protection (AEP) is the only solution that prevents 100% of ransomware and other malware, utilizing a patented, virtual isolation capability that confines unknown files and code in a protective container until it is determined to be 100% safe.
“Once again, Comodo has proven the effectiveness of our solution during this latest evaluation,” said Faith Orhan, EVP of Engineering at Comodo. “As the results of this test illustrate, Comodo is still the only endpoint security solution on the market that applies the Zero Trust principle of ‘Never Trust; Always Verify.”
Infor Partner Event London 2022
June 20th, 2022 by Stephen Jones No comments »A packed day at the Sofitel in London with Infor SunSystems partners from 14 different countries in attendance. Infor has recently set up an internal dedicated IBU for Sunsystems and the management team is moving the solution forwardly rapidly.
While Infor cloud is at the heart of many developments in response to customer demand, there is still an on-premise option that is also being enhanced at the next release.
Expect Infor cloud 12 GA release around October this year.
For smaller customers we expect considerable license simplification for the cloud to be introduced next year.

We expect customer events for Infor SunSystems later this year.
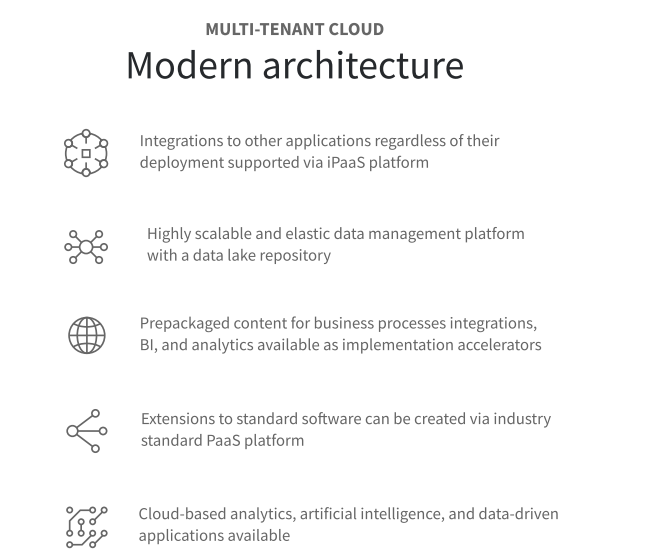
Sunsystems powerful financial features and the journey to Infor Cloud is summarised below:
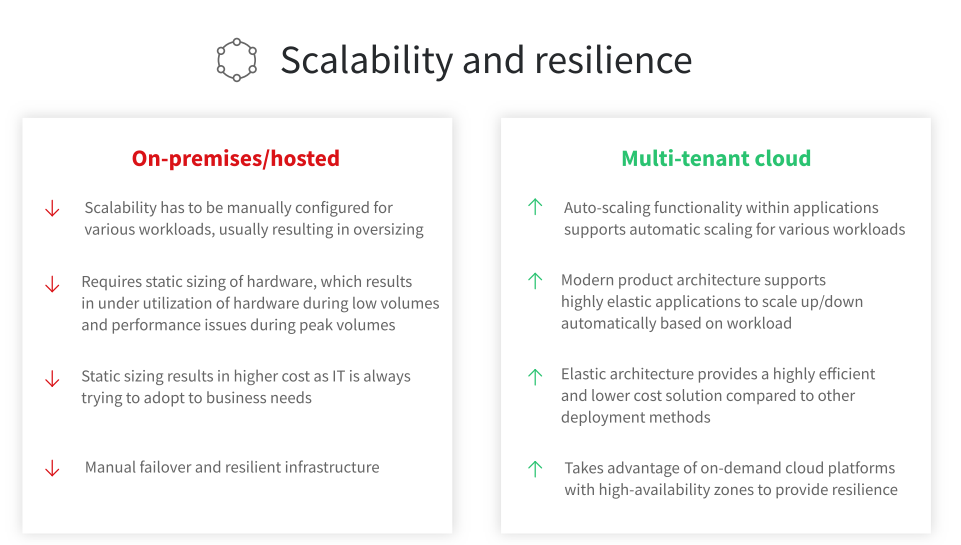
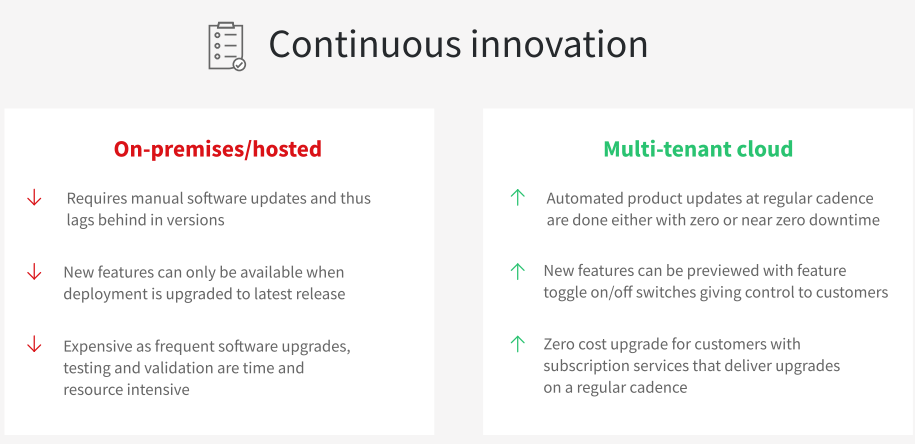
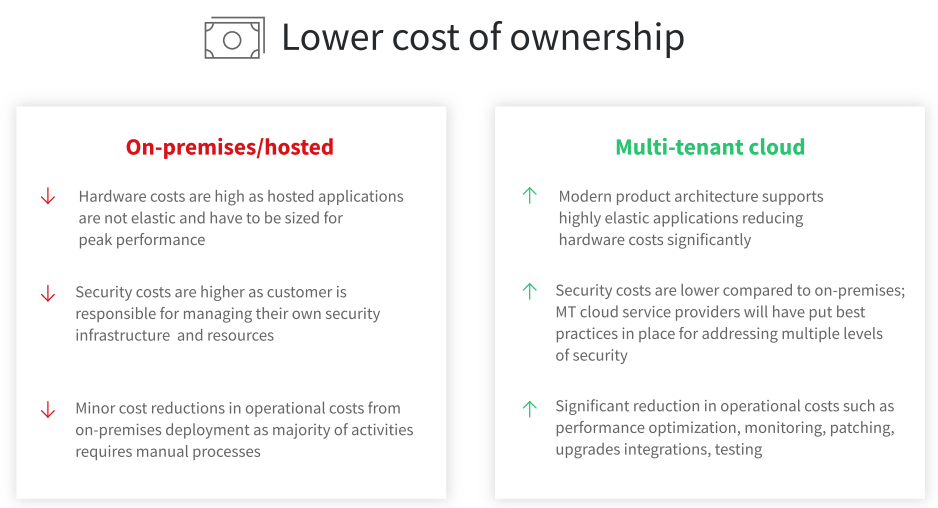
Secure business continuity for the office of the CFO in the cloud
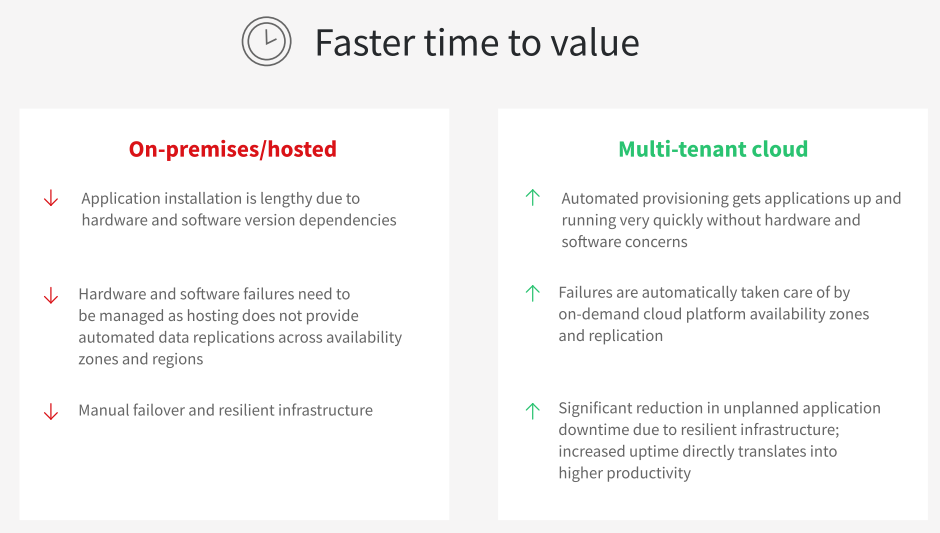
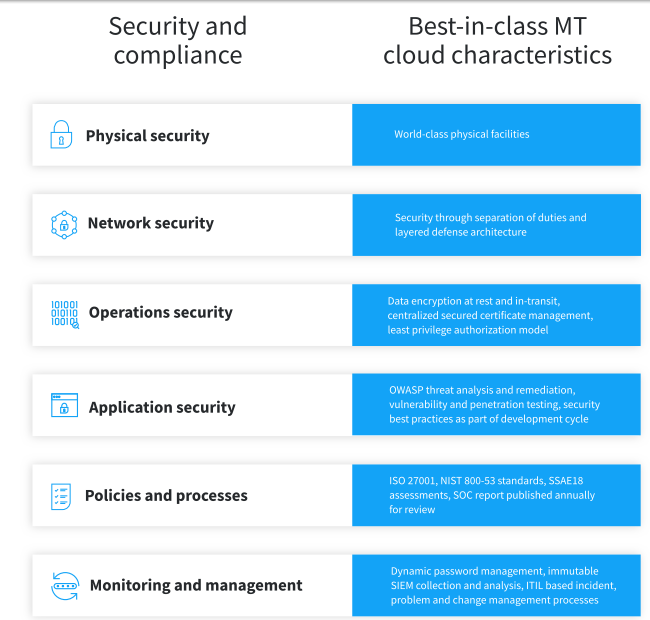
When you move to the Infor Cloud, your organization will benefit from continuous technology enhancements without disruption, replace legacy customizations with Infor’s deep industry functionality, gain world-class security, improve uptime and reduce risk.
Synergy Software Systems has been an Infor partner since its inception 20 years ago a Sun Systems partner for almost 30 years.
To learn more about SunSystems on-premise, or on cloud call us 00971 4 3365589
Goodbye Internet explorer.
June 18th, 2022 by Stephen Jones No comments »it might have been your first ever web browser but – after 27 long years – Microsoft is no longer supporting Internet Explorer. Microsoft previously planned to pull support last August by when its usage had shrivelled
Microsoft says that Edge is “a faster, more secure and more modern browsing experience than Internet Explorer”, as well as one that crucially remains compatible with “older, legacy websites and applications”.
.
June 2022 cumulative Windows Update to seal the zero-day security hole
June 18th, 2022 by Stephen Jones No comments »the June 2022 cumulative Windows Updates seal the zero-day security hole that enabled an exploit called Follina (CVE-2022-30190).
The security flaw was in a Microsoft Windows Support Diagnostic Tool (MSDT) remote code execution bug, which allows hackers to execute arbitrary code within apps by using the tool, such as installation of programs, change or deletion of data or creation of a new Windows account with a compromised user’s rights on the affected PC.
The bug affects machines running Windows 7 and later.
The bug appears to have been exploited by Chinese hackers to send malicious documents to Tibetans. and also to target U.S. and European Union government agencies.
Other cyber-savvy criminals could use the same exploit on unpatched PCs to cause havoc. so we like Microsoft, recommend that you ensure your PC is patched as soon as possible.
“Microsoft strongly recommends that customers install the updates to be fully protected from the vulnerability. Customers whose systems are configured to receive automatic updates do not need to take any further action,” said Microsoft.
With automatic updates enabled you should already protected. If not then to ensure you have the latest patch go to the Windows Settings app, navigate to the Windows Update section to see whether your PC is up to date,, or needs an update, or in some cases a restart to apply the update.
Do this to keep your PC protected from malicious and opportunistic hackers.
Beware spam email attachments
June 14th, 2022 by Stephen Jones No comments »Gmail, Hotmail, Outlook and other users could be exposed to spam emails that could break their Windows, PC with just one click. The dangerous malware on the spam email could steal sensitive personal and financial, data and also steal credentials for Windows and banking services.
Security experts warn that threat actors are taking advantage of a vulnerability that hasn’t yet been fixed by Microsoft to distribute the dangerous Qbot banking trojan malware .
This malicious software has been found in infected Word documents that are spread by email.
The Qbot malware also a allows bad actors to deploy a backdoor on infected Windows machines and to give remote access to ransomware gangs.
Scammers try to trick people to click on the infected attachment by sending fake invoices, payment and banking details, scanned documents or bills. One scam even suggested that people had received a pay rise.
To help keep safe from these threats, do not click on unsolicited emails from unknown addresses , and especially not on any links or attachments in such messages.
‘You can usually identify a scam by taking a close look at a sender’s email address,
Cybercrime update – increasingly scary
June 13th, 2022 by Stephen Jones No comments »According to the recent “2022 Ransomware Trends Report” (Veeam), compiled by surveying 1,000 global IT leaders, paying a ransom for an organization’s hijacked data doesn’t ensure return of the stolen data.
- 24 percent of organizations that paid the amount demanded by ransomware attackers ended up not recovering their stolen data.
- 19 percent of those affected by ransomware were able to recover their data through their own means and without having to pay off the attackers.
- When data is eventually recovered after remediation through payment, data recovery took an average of 18 days.
- (22 percent) reported it took one to two months to fully recover the data,
- 3 percent said they were down for two to four months.
- Some time was spent decrypting the encrypted stolen data, but much of the downtime is attributed to deep scans of restored systems to confirm they were “clean” from any ransomware remnants.
- Backup repositories were targeted 94 percent of the time.
- Specific production platforms or application types were targeted in 80 percent of successful ransomware attacks, making ransomware prevention not just the duty of IT security
- Phishing e-mails and malicious links and Web sites continue to be the top (44 percent) ransomware entry points,
- Infected patches and software are close behind with 41 percent of all ransomware attacks by those surveyed.
- The remaining entry point sources:
- Compromised credentials and spraying attacks (35 percent).
- Insider threats (32 percent).
- Zero-day vulnerabilities (26 percent).
- Only 1 percent of those who experienced a ransomware attack were not able to identify the entry point
About 25 years ago a business report indicated that a majority of companies that lost their computer system for more than one week went out of business within 18 months. A sobering thought given our increased dependence on systems in the digital age, and the surge in state sponsored cybercrime.
The 2022 Ransomware Trends Report” indicates that most organizations don’t have the tools or know-how to recover their hijacked data before they end up paying for their data back.
- A strong Modern Data Protection strategy requires a commitment to a clear policy that the organization will never pay the ransom, but do everything in its power to prevent, remediate and recover from attacks,.
- IT should routinely test their data protection solutions and protocols and ensure that employees are well-versed in spotting possible ransomware attacks.
Veeam credits the improvements in monitoring tools and a concerted effort toward ransomware prevention by many IT shops for the high success in identifying the source of ransomware.
The report finds that.
“This alone should drive broader conversations within IT, so cyber security isn’t just the delegated to the security team; database administrators should also help ensure that database servers are secure and administrators should help ensure hypervisors are patched, that Windows updates are routinely run, etc.,”
How to protect yourself against ransomware
Whether a simple ransomware attack, a double- or triple-extortion attack, a self-contained threat family, or a RaaS attack executed by an affiliate network, the defense strategy is the same: employ the principles of zero trust to limit vulnerabilities, prevent and detect attacks, and limit the blast radius of successful breaches.
Here are some best practices recommendations to safeguard your organization against ransomware:
- Get your applications off of the internet. Ransomware actors start their attacks by performing reconnaissance on your environment, looking for vulnerabilities to exploit, and to calibrate their approach. The more applications you have published to the internet, the easier you are to attack.
- Use a zero trust architecture to secure internal applications, make those invisible to attackers.
- Enforce a consistent security policy to prevent initial compromise. With a distributed workforce, it is important to implement a security services edge (SSE) architecture that can enforce consistent security policy no matter where your users are working (in office or remotely).
- Use sandboxing to detect unknown payloads. Signature-based detection is not enough in the face of rapidly changing ransomware variants and payloads. Protect against unknown and evasive attacks with an inline, AI-powered sandbox that analyzes the behavior rather than the packaging of a file.
- Implement a zero trust network access (ZTNA) architecture. Implement granular user-to-application and application-to-application segmentation, brokering access using dynamic least-privileged access controls to eliminate lateral movement. This allows you to minimize the data that can be encrypted or stolen, reducing the blast radius of an attack.
- Deploy inline data loss prevention. Prevent exfiltration of sensitive information with trust-based data loss prevention tools and policies to thwart double-extortion techniques.
- Keep software and training up to date. Apply software security patches and conduct regular security awareness employee training to reduce vulnerabilities that can be exploited by cybercriminals.
- Have a response plan. Prepare for the worst with cyber insurance, a data backup plan, and a response plan as part of your overall business continuity and disaster recovery program.
- To strengthen defences against ransomware, embrace layered defenses that can disrupt the attack at each stage—from reconnaissance to initial compromise, lateral movement, data theft, and ransomware execution.
The amount of time cyber criminals intruders are spending inside victims’ networks is increasing, providing them with the ability to carry out higher complexity campaigns and more damaging cyber attacks.
According to analysis by cybersecurity researchers at Sophos, who examined incidents targeting organisations around the world and across a wide range of industry sectors, the median dwell time which cyber criminals spend inside compromised networks is now 15 days, up from 11 days the previous year.
The 2022 ThreatLabz State of Ransomware report breaks down a year’s worth of intelligence from a variety of sources, including over 200 Billion daily transactions and 150M daily blocked threats across the Zscaler Zero Trust Exchange, and shows that ransomware is becoming even more attractive to criminals. Attackers are able to wage increasingly profitable campaigns based on three major trends:
- Supply chain attacks,
- ransomware-as-a-service ecosystems,
- multi-extortion tactics.
Ransomware attacks increased by 80% year-over-year, accounting for all ransomware payloads observed in the Zscaler cloud.
- Double extortion ransomware overall increased by 117%.
- Manufacturing was the most targeted industry for the second year running, – almost 20% of double-extortion ransomware attacks.
Some industries saw particularly high growth of double-extortion attacks, including:
- healthcare (643%),
- food service (460%),
- mining (229%),
- education (225%),
- media (200%),
- manufacturing (190%).
Some recent events………
The DeadBolt ransomware started 2022 with attacks that targeted internet-facing Network-Attached Storage (NAS) devices.
- First target was QNAP Systems, Inc. in January 2022. According to a report from Censys.io, Jan. 26, 2022, out of 130,000 QNAP NAS devices that were potential targets, 4,988 services showed signs of a DeadBolt infection.
- ASUSTOR, another NAS devices and video surveillance solutions vendor, also experienced DeadBolt ransomware attacks that targeted an unknown number of its devices.
- In March, DeadBolt attackers again targeted QNAP devices; and the number of infections reached 1,146 by March 19, 2022.
- On May 19,2022, QNAP released a product security update stating that internet-connected QNAP devices were again bargeted by DeadBolt, this time aiming at NAS devices using QTS 4.3.6 and QTS 4.4.1.
- The number of DeadBolt-infected devices is very high for a ransomware family that exclusively targets NAS devices.
LockBit 2.0 is ransomware as a service (RaaS)
- This first emerged in June 2021 as an upgrade to its predecessor LockBit (aka ABCD Ransomware), which was first observed in September 2019.
- Since its inception, the LockBit 2.0 RaaS attracted affiliates via recruitment campaigns in underground forums, and thus became particularly prolific during the third quarter of calendar year 2021. The LockBit 2.0 operators claimed to have the fastest encryption software of any active ransomware strain as of June 2021, claiming accordingly that this added to its effectiveness and ability to disrupt the ransomware landscape.
An ongoing phishing campaign targeting Facebook users may have already netted hundreds of millions of credentials and a claimed $59 million, and it’s only getting bigger.
- Identified by security researchers at phishing prevention company Pixm in late 2021, the campaign has only been running since the final quarter of last year, but has already proven incredibly successful. Just one landing page – out of around 400 Pixm found – got 2.7 million visitors in 2021, and has already tricked 8.5 million viewers into visiting it in 2022.
- The flow of this phishing campaign isn’t unique: Like many others targeting users on social media, the attack comes as a link sent via DM from a compromised account.
The Vice Society ransomware group has claimed responsibility for the recent cyber attack on the city of Palermo in Italy, which has caused a large-scale service outage.
- The attack occurred last Friday, and all internet-relying services remain unavailable, impacting 1.3 million people and many tourists visiting the city.
- The authorities admitted the severity of the incident on Monday and explained that all systems had to be taken offline to contain the damage, warning that the outages might last a few more days.
Shields Health Care Group Inc., which provides imaging and ambulatory surgical services at dozens of locations, said in a notice on its website Tuesday that data including names, Social Security numbers, dates of birth, and medical or treatment details is among the information that may have been compromised.
- The breach has been reported to federal law enforcement and the U.S. Department of Health and Human Services Office for Civil Rights.
- That agency reported on its website that 2 million people were affected.
- An FBI spokesperson said the agency had no comment.
The Cuba ransomware operation has returned to regular operations with a new version of its malware found used in recent attacks.
- Cuba ransomware’s activity reached a peak in 2021 when it partnered with the Hancitor malware gang for initial access.
- By the end of the year, it had breached 49 critical infrastructure organizations in the United States.
Russia-Ukraine
The Kremlin-backed cyberattack against satellite communications provider Viasat, which happened an hour before Russia invaded Ukraine, was “one of the biggest cyber events that we have seen, perhaps ever, and certainly in warfare,” according to Dmitri Alperovitch, co-founder of CrowdStrike and chair of security-centric think tank Silverado Policy Accelerator.
- An obvious purpose of the attack was to disrupt Ukrainian communications during the invasion, by wiping the modems’ firmware remotely, it also disabled thousands of small-aperture terminals in Ukraine and across Europe.
- The attack disrupted satellite connectivity for thousands, and disabled remote monitoring of 5,800 wind turbines in Germany.
The Russia-Ukraine conflict has the world on high alert.
- Several attacks associated with the Russia-Ukraine conflict, combined multiple tactics, such as HermeticWiper and PartyTicket ransomware.
- Most of this activity has targeted Ukraine.
- Government agencies have warned organizations to be prepared for more widespread attacks as the conflict persists.
Microsoft has obtained a court order to seize 41 domains used by what the Windows giant said was an Iranian cybercrime group that ran a spear-phishing operation targeting organizations in the US, Middle East, and India.
- The Microsoft Digital Crimes Unit said the gang, dubbed Bohrium, took a particular interest in those working in technology, transportation, government, and education sectors: its members would pretend to be job recruiters to lure marks into running malware on their PCs.
- “Bohrium actors create fake social media profiles, often posing as recruiters,” said Amy Hogan-Burney, GM of Microsoft’s Digital Crimes Unit. “Once personal information was obtained from the victims, Bohrium sent malicious emails with links that ultimately infected their target’s computers with malware.”
Last month the notorious Russian ransomware gang Conti threatened that if a ransom wasn’t paid it would overthrow Costa Rica’s government.
This month, the Hive ransomware gang hit Costa Rica’s Social Security system, and also struck the country’s public health agency, which had to shut down its computers on Tuesday to prevent the spread of a malware outbreak.
The Costa Rican government said at least 30 of the agency’s servers were infected, and its attempt at shutting down systems to limit damage appears to have been unsuccessful. Hive is asking for $5 million in Bitcoin to unlock infected systems.
As ransomware becomes less profitable or carries a higher risk for attackers It is logical for ransomware actors to eventually convert their operations to business email compromise (BEC) attacks.
In the US, the Federal Bureau of Investigation has repeatedly found that total money stolen in BEC scams far exceeds that pilfered in ransomware attacks—though ransomware attacks can be more visible and cause more disruption and associated losses.
The newer Industrial Spy group is applying greater pressure on victims by hacking their websites to display ransom notes.
The Canadian Department of National Defence confirmed recently that a key supplier – CMC Electronics a key supplier to a critical defence initiative.– reported that they were victim of a ransomware attack.
- CMC makes cockpit systems integration, avionics, display solutions, and high-performance microelectronics for military and commercial aircraft.
- It was recently selected to supply the avionics and software applications for the Royal Canadian Air Force’s new Calidus B-250 turboprop light attack combat and training aircraft
- It was reportedly attacked by a gang calling itself AlphV. The FBI say the gang also operate under the name BlackCat. and had compromised over 60 organizations worldwide as of March of this year.
Power Bi and integration with Dynamics 365 and Microsoft 365
June 12th, 2022 by Stephen Jones No comments »#Online #FREE session Power BI & Microsoft 365 – Better Together by Amanda Riveria Principal Program Manager at Microsoft – 16th June
Power BI & Microsoft 365 – Better Together
“Businesses looking to gain an edge in today’s competitive market need to harness the power of their data to make informed decisions that drive innovation across their entire company. Information workers, not just analysts and data scientists, need to be empowered to use their data in a familiar environment, securely and easily. Join this session to see how Power BI’s integrations across many M365 products can enhance your organization’s self-service data culture and reduce time to insights. We’ll cover integrations across Excel, Dynamics 365, Teams, and more!”